-
Taipei, Taiwan, January 7, 2022 – QNAP® Systems, Inc. (QNAP) today issued a product security statement. Ransomware and brute-force attacks have been widely targeting all networking devices, and the most vulnerable victims will be those devices exposed to the Internet without any protection. QNAP urges all QNAP NAS users to follow the security setting instructions below to ensure the security of QNAP networking devices.
Check whether your NAS is exposed to the Internet
Open the Security Counselor on your QNAP NAS. Your NAS is exposed to the Internet and at high risk if there shows “The System Administration service can be directly accessible from an external IP address via the following protocols: HTTP” on the dashboard.
- How to know which ports on the router are exposed to the Internet:
https://www.qnap.com/go/how-to/faq/article/how-to-know-which-ports-on-the-router-are-opened-to-the-internet
If your NAS is exposed to the Internet, please follow the instructions below to ensure NAS security:
Step 1: Disable the Port Forwarding function of the router
Go to the management interface of your router, check the Virtual Server, NAT or Port Forwarding settings, and disable the port forwarding setting of NAS management service port (port 8080 and 433 by default).
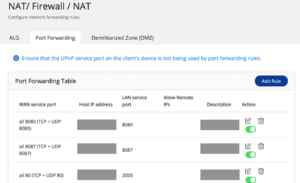
Step 2: Disable the UPnP function of the QNAP NAS
Go to myQNAPcloud on the QTS menu, click the “Auto Router Configuration”, and unselect “Enable UPnP Port forwarding”.
- Securely access your QNAP NAS via the Internet through myQNAPcloud Link:
https://www.qnap.com/go/solution/myqnapcloud-link/ - Learn more about NAS remote access and network security:
https://www.qnap.com/go/solution/secure-remote-access/
- How to know which ports on the router are exposed to the Internet:

- Navigation
- Home
- Chi siamo
- » Perché noi
- Prodotti
- » Netwrix
- » Altaro
- » Stormshield
- » Microsoft Office 365
- » Mailstore
- » Kaspersky
- » Overland Tandberg
- » N-Able
- » Eaton
- » Nec Centralini Ibridi e Cloud
- » HP Inc
- » HP Enterprise
- » Engenius Network
- » Logitech Videoconference
- » D-Link
- Servizi
- » Network Services
- » Cloud
- » IT Consulting
- » Maintenance
- » Communication
- Clienti
- Blog
- Alert
- Contatti
Avete bisogno di una soluzione ? Chiamateci al num. 010 383532
Chi siamo
ITSoluzioni Srl, Azienda di Servizi e Soluzioni Informatiche
Via delle Genziane 128R, 16148 Genova
carozzo@itsoluzioni.it
010 383532Iscrizione Newsletter

{ITSoluzioni Srl} | @ 2022